Wildfly 10 with Kerberos SSO and Waffle SSO configuration
The web application with the Kerberos implementation will use the Windows logged-in user and will authenticate in Kerberos way.
To perform Kerberos Authentic there are some pre-requisites to be fulfilled as given below
1. Kerberos Authentication is used in the Intranet environment, where Microsoft Active Directory, Application Server and Client accessing the application should on the same domain. This authentication is done with the Microsoft Active Directory.
2. The user accessing the application should be present in the Active Directory server.
3. If the client accessing the application is not in the domain then the application will prompt for a username and password popup.
4. Keytab file generated from Active Directory using admin user. This keytab file should be generated with the same hostname where the application server resides
5. Application on Wildfly server up and running.
6. Application server and Active Directory on the same domain.
7. Client should be a member of the same Active Directory Domain as the Application Server.
Perform the below steps to configure Kerberos SSO on Wildfly Application Server:
1. Add Security Domain SPNEGO(Simple and Protected GSSAPI Negotiation Mechanism)
used to authenticate secured resources and negotiate securely.
Add below security-domain in jboss-web.xml
Path : {Application -Home}\Web-Inf\jboss-web.xml
<security-domain>SPNEGO</security-domain>
This allows the application to use the SPNEGO login module configured in the security domain.
2. Add Security constraint in web.xml
Path : {Application -Home}\Web-Inf\web.xml
<security-constraint> <display-name>excluded</display-name> <web-resource-collection> <web-resource-name>No Access</web-resource-name> <url-pattern>*</url-pattern> <http-method>PUT</http-method> <http-method>OPTIONS</http-method> <http-method>DELETE</http-method> <http-method>CONNECT</http-method> <http-method>PATCH</http-method> <http-method>PROPFIND</http-method> <http-method>PROPPATCH</http-method> <http-method>MKCOL</http-method> <http-method>COPY</http-method> <http-method>MOVE</http-method> <http-method>LOCK</http-method> <http-method>UNLOCK</http-method> <http-method>TRACE</http-method> </web-resource-collection> <web-resource-collection> <web-resource-name>Restricted</web-resource-name> <url-pattern>/Myurl</url-pattern> <http-method>GET</http-method> <http-method>POST</http-method> </web-resource-collection> <auth-constraint> <role-name>*</role-name> </auth-constraint> </security-constraint>
<login-config> <auth-method>SPNEGO</auth-method> </login-config>
<security-role> <description>security role</description> <role-name>*</role-name> </security-role>
The first web resource restricts the mentioned methods.
3. Configure KDC and keytab in Wildfly Application Server
Add below system properties in standalone-full.xml
Path : {Wildfly-Home}/standalone/configuration/standalone-full.xml
<system-properties> <property name="sun.security.krb5.debug" value="true" /> <property name="java.security.krb5.realm" value="DOMAIN.IN" /> <property name="java.security.krb5.kdc" value="SERVER.DOMAIN.IN" /> </system-properties>
e.g.
<property name="sun.security.krb5.debug" value="true"/>
Where keyTab will have keytab file path and principal will have SPN given while creating keytab file.
3) Now create a servlet filter that extends NegotiateSecurityFilter
in the doFilter() of this servlet filter call superclass filter like
super.doFilter(a_servletRequest, a_servletResponse, a_filterChain);
4) Map this filter to all URLs in web.xml or just login page based on the requirement.
5) Now to access the logged-in user use the below snippet.
request.getRemoteUser();
Thats it!!!!!!!!!!!!!!
To perform Kerberos Authentic there are some pre-requisites to be fulfilled as given below
1. Kerberos Authentication is used in the Intranet environment, where Microsoft Active Directory, Application Server and Client accessing the application should on the same domain. This authentication is done with the Microsoft Active Directory.
2. The user accessing the application should be present in the Active Directory server.
3. If the client accessing the application is not in the domain then the application will prompt for a username and password popup.
4. Keytab file generated from Active Directory using admin user. This keytab file should be generated with the same hostname where the application server resides
5. Application on Wildfly server up and running.
6. Application server and Active Directory on the same domain.
7. Client should be a member of the same Active Directory Domain as the Application Server.
Perform the below steps to configure Kerberos SSO on Wildfly Application Server:
1. Add Security Domain SPNEGO(Simple and Protected GSSAPI Negotiation Mechanism)
used to authenticate secured resources and negotiate securely.
Add below security-domain in jboss-web.xml
Path : {Application -Home}\Web-Inf\jboss-web.xml
<security-domain>SPNEGO</security-domain>
This allows the application to use the SPNEGO login module configured in the security domain.
2. Add Security constraint in web.xml
Path : {Application -Home}\Web-Inf\web.xml
<security-constraint> <display-name>excluded</display-name> <web-resource-collection> <web-resource-name>No Access</web-resource-name> <url-pattern>*</url-pattern> <http-method>PUT</http-method> <http-method>OPTIONS</http-method> <http-method>DELETE</http-method> <http-method>CONNECT</http-method> <http-method>PATCH</http-method> <http-method>PROPFIND</http-method> <http-method>PROPPATCH</http-method> <http-method>MKCOL</http-method> <http-method>COPY</http-method> <http-method>MOVE</http-method> <http-method>LOCK</http-method> <http-method>UNLOCK</http-method> <http-method>TRACE</http-method> </web-resource-collection> <web-resource-collection> <web-resource-name>Restricted</web-resource-name> <url-pattern>/Myurl</url-pattern> <http-method>GET</http-method> <http-method>POST</http-method> </web-resource-collection> <auth-constraint> <role-name>*</role-name> </auth-constraint> </security-constraint>
<login-config> <auth-method>SPNEGO</auth-method> </login-config>
<security-role> <description>security role</description> <role-name>*</role-name> </security-role>
The first web resource restricts the mentioned methods.
3. Configure KDC and keytab in Wildfly Application Server
Add below system properties in standalone-full.xml
Path : {Wildfly-Home}/standalone/configuration/standalone-full.xml
<system-properties> <property name="sun.security.krb5.debug" value="true" /> <property name="java.security.krb5.realm" value="DOMAIN.IN" /> <property name="java.security.krb5.kdc" value="SERVER.DOMAIN.IN" /> </system-properties>
e.g.
<property name="sun.security.krb5.debug" value="true"/>
<property name="java.security.krb5.realm" value="mydomain.in"/>
<property name="java.security.krb5.kdc" value="192.168.100.5"/>
If sun.security.krb5.debug this property is set to true then it will enable Kerberos logs in debug mode to ensure this is not set in a production environment.
If sun.security.krb5.debug this property is set to true then it will enable Kerberos logs in debug mode to ensure this is not set in a production environment.
sun.security.krb5.debug this enables debug logs on login.
4. Add Negotiation module
Search for the domain subsystem in the standalone-full.xml then add the negotiation module in the global modules.
No need to create the negotiation module as it comes by default with the Wildfly 10.
Search for the domain subsystem in the standalone-full.xml then add the negotiation module in the global modules.
No need to create the negotiation module as it comes by default with the Wildfly 10.
<subsystem xmlns="urn:jboss:domain:ee:4.0">
<global-modules>
<module name="org.jboss.security.negotiation" slot="main" />
</global-modules>
</subsystem>
5. Add Security Domains in the standalone-full.xml.
This includes the keytab file path, Kerberos domain controller details and other debugging details.
Note: Ensure the keytab file is created with the host name of the application server and also application server and Active Directory server are in the same domain.
<security-domain name="host" cache-type="default"> <authentication> <login-module code="com.sun.security.auth.module.Krb5LoginModule" flag="required"> <module-option name="storeKey" value="true" /> <module-option name="useKeyTab" value="true" /> <module-option name="principal" value="HTTP/mymachine.domain.in@DOMAIN.IN" /> <module-option name="keyTab" value="D:/mykeytab.keytab" /> <module-option name="doNotPrompt" value="true" /> <module-option name="debug" value="true" /> </login-module> </authentication> </security-domain>
This includes the keytab file path, Kerberos domain controller details and other debugging details.
Note: Ensure the keytab file is created with the host name of the application server and also application server and Active Directory server are in the same domain.
<security-domain name="host" cache-type="default"> <authentication> <login-module code="com.sun.security.auth.module.Krb5LoginModule" flag="required"> <module-option name="storeKey" value="true" /> <module-option name="useKeyTab" value="true" /> <module-option name="principal" value="HTTP/mymachine.domain.in@DOMAIN.IN" /> <module-option name="keyTab" value="D:/mykeytab.keytab" /> <module-option name="doNotPrompt" value="true" /> <module-option name="debug" value="true" /> </login-module> </authentication> </security-domain>
Where keyTab will have keytab file path and principal will have SPN given while creating keytab file.
<security-domain name="SPNEGO" cache-type="default">
<authentication>
<login-module code="org.jboss.security.negotiation.spnego.SPNEGOLoginModule" flag="required">
<module-option name="password-stacking" value="useFirstPass" />
<module-option name="serverSecurityDomain" value="host" />
</login-module>
</authentication>
</security-domain>
6. Restart the Wildfly server.
7. Access the application with the hostname instead of the IP address of the server.
Some browsers will need URL configuration as shown below.
7. Access the application with the hostname instead of the IP address of the server.
Some browsers will need URL configuration as shown below.
This also requires browser configuration
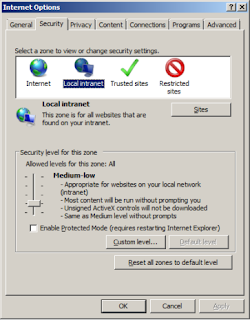
1. Internet Explorer
a. On the Tools menu, click Internet Options.
The Internet Options dialog, and click the Security tab.
In the Security tab, make sure the Local intranet icon is selected and click the Sites button.
In the Local intranet dialog, enter the URL of the server with the JBoss installation and click Add.
Firefox Settings:
a. Navigate to the about:config URL with the configuration options for Firefox.
Troubleshooting
1. [org.jboss.security.negotiation.spnego.SPNEGOLoginModule] Unsupported negotiation mechanism 'NTLM'.
Resolution
Try with hostname.domain and not with IP address
Ensure it is added in firefox about:config
There is an alternative for Intranet Authentication i.e. WAFFLE framework which uses Windows libraries and does not require all these configurations but only works on Windows.
There is an alternative for Intranet Authentication i.e. WAFFLE framework which uses Windows libraries and does not require all these configurations but only works on Windows.
WAFFLE SSO with WILDFLY
Waffle is another alternative to Intranet SSO Authentication. Instead of doing all the configuration this library will use the native DLLs and do authentication Kerberos way. But this will only work on Windows systems.
Steps
1. Download waffle-jna jar from maven repository.
2. Create a module in Wildfly for Waffle
Path : {Wildfly-Home}/modules/
Create a folder inside this named "waffle" and create folder name "main" inside waffle folder and create a module.xml with the below content and place the jar file in the same folder.
Path : {Wildfly-Home}/modules/
Create a folder inside this named "waffle" and create folder name "main" inside waffle folder and create a module.xml with the below content and place the jar file in the same folder.
<?xml version="1.0" encoding="UTF-8"?>
<module xmlns="urn:jboss:module:1.1" name="waffle">
<properties>
<property name="jboss.api" value="private"/>
</properties>
<resources>
<resource-root path="waffle-jna-1.8.3.jar"/>
</resources>
<dependencies>
<module name="com.google.guava"/>
<module name="com.sun.jna"/>
<module name="org.slf4j.jcl-over-slf4j"/>
<module name="org.slf4j"/>
<module name="javax.servlet.api"/>
<module name="javax.servlet.jsp.api"/>
<system export="true">
<paths>
<path name="javax/security/auth"/>
</paths>
</system>
</dependencies>
</module>
in the doFilter() of this servlet filter call superclass filter like
super.doFilter(a_servletRequest, a_servletResponse, a_filterChain);
4) Map this filter to all URLs in web.xml or just login page based on the requirement.
5) Now to access the logged-in user use the below snippet.
request.getRemoteUser();
Thats it!!!!!!!!!!!!!!




On which wildfly do you test this solution? 10.0.0.Final or 10.1.0.Final? This soultion seems doesn't work on 10.0.0.Final.
ReplyDeleteI have done this on Wildfly 10.1.0
Deletemagnificent post, very informative. I'm wondering why the other specialists of this sector do not realize this. You must proceed your writing. I'm confident, you've a great readers' base already! Recomendation for you สล็อ
ReplyDelete